SSH Tunneling
SSH tunneling is used to send requests from your SSH client to the SSH server such as forwarding local services for external access or creating a SOCKS proxy.
They are really useful and an amazing tool if you aren’t already using them.
Basic SOCKS proxy tunnel
You can use a dynamic SSH tunnel as a SOCKS proxy. This way you can access sites and services that may be restricted on your local network but not on your servers.
ssh -D 1234 [email protected]You can then set the proxy up in Firefox:
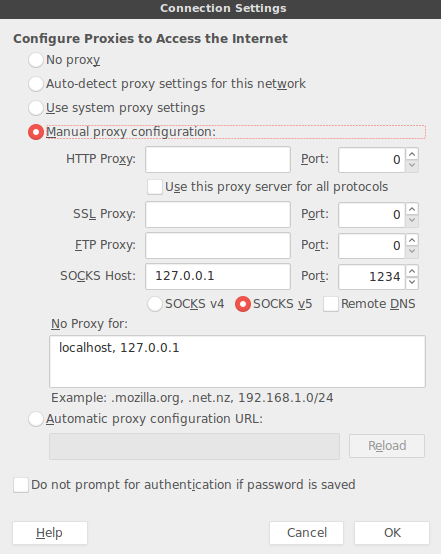
Then check your IP on http://whatismyip.com or similar and it should be your servers, marking a successful tunnel
Forward a local port
You can forward a local port on your server to your local PC. This can be used for things such as web based administration panels that only run on localhost or local MySQL servers.
ssh -L 1235:localhost:3306 [email protected]This will forward remote port 3306 (MySQL) to port 1235 on your local machine. Which for example you could then connect to with mysql --host=localhost --port=1235 --user=root --password
Conclusion
So that should get you started on SSH tunneling. Its a great tool when working with remote servers so try it out!